CyberSec: Difference between revisions
Created page with " == Building a RHEL like env == dnf update -y dnf install hydra gobuster wafw00f whatweb golang git -y git clone https://github.com/tomnomnom/hacks.git cd hacks/html-tool go build -o html-tool main.go cp html-tool /usr/local/bin wget https://files.pedromussato.com/programs/burpsuite_community_linux_v2024_8_2.sh chmod +x burpsuite_community_linux_v2024_8_2.sh ./burpsuite_community_linux_v2024_8_2.sh == Mapping host == === Mapping open ports on host === nmap -D..." |
No edit summary |
||
| Line 120: | Line 120: | ||
root@sadfasdf:~# | root@sadfasdf:~# | ||
=== Get attributes from HTML === | |||
==== Get comments from html ==== | |||
echo '<nowiki>http://domain.com'</nowiki> | html-tool comments | |||
This will return all comments from the page on '<nowiki>http://domain.com'</nowiki>. | |||
==== Get content from html tag ==== | |||
echo '<nowiki>http://domain.com'</nowiki> | html-tool tags <tag 1> <tag 2> ... | |||
This will return all content from the tags specified on the page on '<nowiki>http://domain.com'</nowiki>. | |||
==== Get content from html attributes ==== | |||
echo '<nowiki>http://domain.com'</nowiki> | html-tool attribs <attr 1> <attr 2> ... | |||
This will return all content from the attributes specified on the page on '<nowiki>http://domain.com'</nowiki>. | |||
Revision as of 02:20, 7 October 2024
Building a RHEL like env
dnf update -y dnf install hydra gobuster wafw00f whatweb golang git -y git clone https://github.com/tomnomnom/hacks.git cd hacks/html-tool go build -o html-tool main.go cp html-tool /usr/local/bin wget https://files.pedromussato.com/programs/burpsuite_community_linux_v2024_8_2.sh chmod +x burpsuite_community_linux_v2024_8_2.sh ./burpsuite_community_linux_v2024_8_2.sh
Mapping host
Mapping open ports on host
nmap -D RND:20 --open -sS --top-ports=100 domain.com -oN open-ports.file
- nmap - the comand
- -D RND:20 - will generate 20 random IPs to send the request, to try to mask the requests if there is a inteligent firewall on the other side.
- --open - to get open ports
- -sS - SYN scan the target responds with a SYN-ACK packet (acknowledging the connection)
- --top-ports=100 - list the top 100 ports
- domain.com the host you want to map
- -oN - output name, or, output save to the file named open-ports.file
Optionals
- -p- - will scan all 65535 ports of the server
- --min-rate=N - will send N packages per second
Mapping services on ports
nmap --open -sV -pP1,P2... domain.com -oN services-on-ports.file
- -sV - to scan the service on the port (scan version)
- -pP1,P2 - scan just port P1 and P2 but you can use any number of ports (e.g. -p80,443,22)
Search exposed interfaces
gobuster dir -u http://dominio.com/ -w /word-list.txt -t 100 -e --no-error -r -o exposed-interfaces.file
- gobuster - the command
- dir - uses directory/file enumeration mode
- -u - URL
- -w - word list
- -t 100 - uses 100 paralel threads for reducing search time
- -e - shows extended log
- --no-error - do not returns errors
- -r - follow redirects
- -o exposed-interfaces.file - save output to exposed-interfaces.file
FTP brute force test
hydra -v -t10 -l user -p password ftp://domain.com -s PORT
or
hydra -v -t10 -L /users-list.file -P /passwords-list.file -s PORT
- hydra - the command
- -v - verbose
- -t10 - use 10 threads to make things quickly
- -l - use a specific username
- -L - use a list of usernames
- -p - use a specific password
- -P - use a list of passwords
- -s - specify the port, if not will use the default one (21)
WEB brute force test
Install Burp Suite, go to intercept and turn it on, open the browser,

access the login interface, intercept the request that sends the authentication, send it to repeater and instruder,

then go to the repeater and repeat many times to test if the application is susceptible to brute force attacks,

then go to the intruder > positions and put a §§ on the password field,
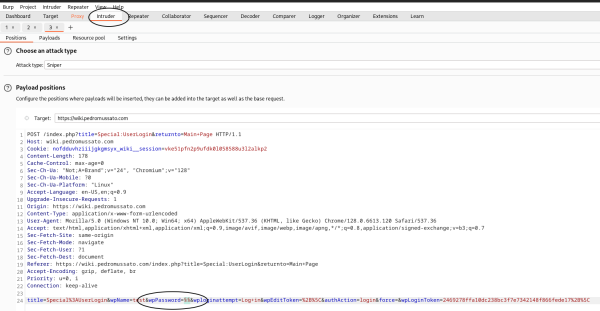
then go to payloads, set payload type to runtime file and then select a file with the password

result:

14 requests in a row and none was blocked by brute force tests.
Checking WAF
wafw007f -v http://domain.com
or
wafw007f -vv http://domain.com
or
wafw007f -vvv http://domain.com
- wafw007f - the command
- -v - verbose level 1
- -vv - verbose level 2
- -vvv - verbose level 3
Checking server details
whatweb http://domain.com
- whatweb - the command
(e.g.)
root@sadfasdf:~# whatweb http://wiki.pedromussato.com http://wiki.pedromussato.com [301 Moved Permanently] Apache[2.4.58], Country[UNITED STATES][US], HTTPServer[Ubuntu Linux][Apache/2.4.58 (Ubuntu)], IP[34.234.173.224], RedirectLocation[1], Title[301 Moved Permanently] root@sadfasdf:~#
or
nc -v domain.com 80 -C OPTIONS /REALLYANYTHING HTTP/1.0
- nc - the command
- -v - verbose
- 80 - the port
- -C - Send CRLF as line-ending
(e.g.)
root@sadfasdf:~# nc -v wiki.pedromussato.com 80 -C DNS fwd/rev mismatch: wiki.pedromussato.com != ec2-34-234-173-224.compute-1.amazonaws.com wiki.pedromussato.com [34.234.173.224] 80 (http) open OPTIONS /asdasd HTTP/1.0 HTTP/1.1 200 OK Date: Thu, 03 Oct 2024 19:07:03 GMT Server: Apache/2.4.58 (Ubuntu) Allow: GET,POST,OPTIONS,HEAD Content-Length: 0 Connection: close root@sadfasdf:~#
Get attributes from HTML
Get comments from html
echo 'http://domain.com' | html-tool comments
This will return all comments from the page on 'http://domain.com'.
Get content from html tag
echo 'http://domain.com' | html-tool tags <tag 1> <tag 2> ...
This will return all content from the tags specified on the page on 'http://domain.com'.
Get content from html attributes
echo 'http://domain.com' | html-tool attribs <attr 1> <attr 2> ...
This will return all content from the attributes specified on the page on 'http://domain.com'.